How to Configure your Custom Helm Repository ScaleEnterpriseSelf-Hosted
With Okteto you can deploy Helm Charts with one click. A default list of Helm Charts is provided to get you and your team up and running.
You can add your own Helm repositories to Okteto to extend this list. This gives you the same one-click deployment experience with the services that you and your team use. You can use this to simplify onboarding and standarize your dependencies.
In order to add your Helm Charts, you'll need a Helm chart repository index with at least one published chart. Follow this guide to learn how to do it.
Add your repository to Okteto Cloud
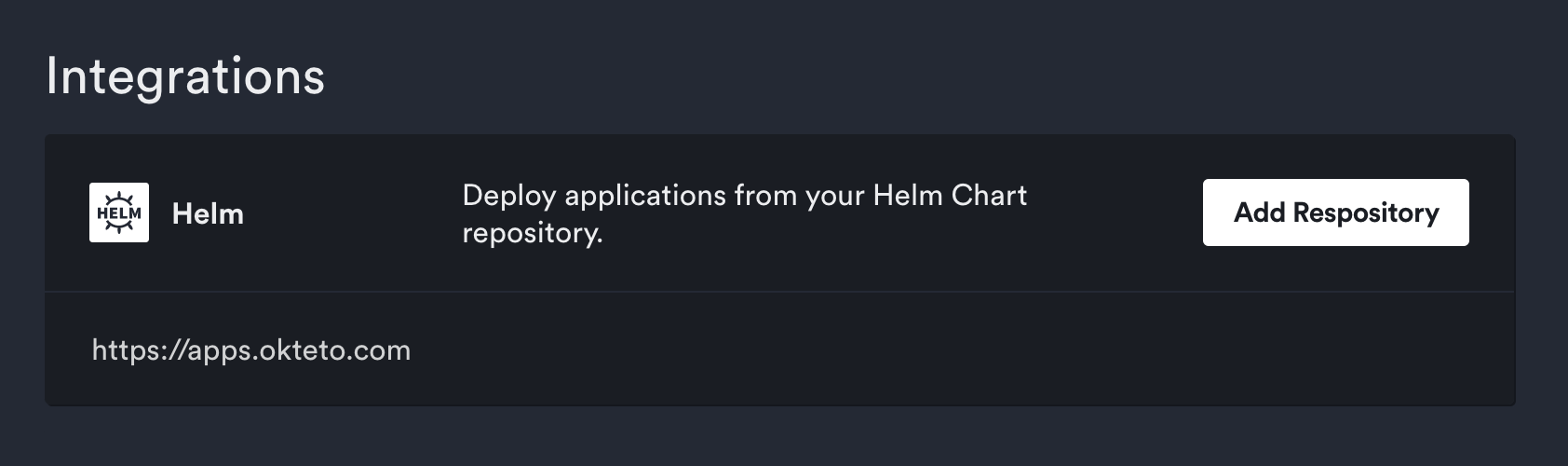
On the left side of the Okteto UI click the Settings option. In the new window, click the Integrations tab. This page will show you the Helm repositories you have configured in Okteto. Click the Add Repository button and put the address of your repository:
The Helm Charts from your Help repository will now be included in the Deploy from Helm Chart dialog.
Suggest default values
The values.yaml file of your Helm Chart contains all the default configuration values for your Helm releases.
This file can be too complex for anyone who is not familiar with your application.
Place a values-okteto.yaml file side by side with your values.yaml file to show the recommended options to the users.
Okteto will automatically load the values-okteto.yaml file and show it in the Deploy from Helm Chart dialog.
Make your chart multi-tenant friendly.
Okteto is a multi-tenant environment. We recommend that you update your charts to take advange of this, and to make them safer and easier to use for everyone.
Your Helm chart will need to comply with these restrictions to function properly with the default permissions in Okteto:
- Your chart cannot create
ClusterRoleorClusterRoleBindingobjects. NodePortandLoadBalancerservice types are not supported. Okteto Cloud automatically translatesNodePortorLoadBalancerservices into ingress rules. More information is available here.- The following
Podoptions are not allowed:privileged,hostNetwork,allowPrivilegeEscalation,hostPID,hostIPC. Volume host paths are not allowed either.
More information about our multi-tenant policies is available here.